
Cloud security is of immediate concern to organisations that must comply with strict confidentiality and integrity policies. More broadly, security has emerged as a commercial imperative for cloud computing across a wide range of markets. The lack of adequate security guarantees is becoming the primary barrier to the broad adoption of cloud computing. The Secure Enclaves for REactive Cloud Applications (SERECA) project aims to remove technical impediments to secure cloud computing, and thereby encourage greater uptake of cost-effective and innovative cloud solutions in Europe. It proposes to develop secure enclaves, a new technique that exploits secure commodity CPU hardware for cloud deployments, empowering applications to ensure their own security without relying on public cloud operators. Secure enclaves additionally support regulatory-compliant data localisation by allowing applications to securely span multiple cloud data centres.
Although secure enclaves are a general mechanism, SERECA focuses on a particularly important and rapidly growing class of applications: reactive applications for the Internet of Things (IoT), Cyber-Physical Systems (CPS), augmented reality, gaming, computer-mediated social interaction, and the like. These applications are highly interactive, data intensive, and distributed, often involving extremely sensitive societal and personal information.
SERECA is validating its results through the development of two innovative and challenging industry-led use cases. One concerns the monitoring of a civil water supply network, a critical infrastructure targeted by malicious attacks. The other concerns a commercial software-as-a-service (SaaS) application for analysing the performance of cloud-deployed applications. Such a service collects sensitive performance metrics about live usage, assets that must be protected from industrial espionage and other criminal activities.
SERECA aims to remove technical impediments to secure cloud computing, and thereby encourage greater uptake of cost-effective and innovative cloud solutions in Europe. It proposes to develop a secure environment for reactive cloud application using the new Intel's CPU extension: Software Guard eXtension (SGX). SERECA will allow the execution of sensitive code on Cloud platforms, without the need of trusting the public cloud operators. Furthermore, SERECA will support regulatory-compliant data localisation by allowing applications to securely span multiple cloud data centers.
| Titel | Art | Betreuer | Status |
|---|---|---|---|
| Schnelle Inter-Enklaven Kommunikation mit Intel SGX, ... | Masterarbeit | Dr. Nico Weichbrodt | abgeschlossen |
| Portierung einer minimalen Java Laufzeit-Umgebung auf eine Intel SGX Plattform, ... | Masterarbeit | Dr. Nico Weichbrodt | abgeschlossen |
| Design and implementation of trusted applications applying the ARM TrustZone hardware extensions | Masterarbeit | Dr. Stefan Brenner | abgeschlossen |
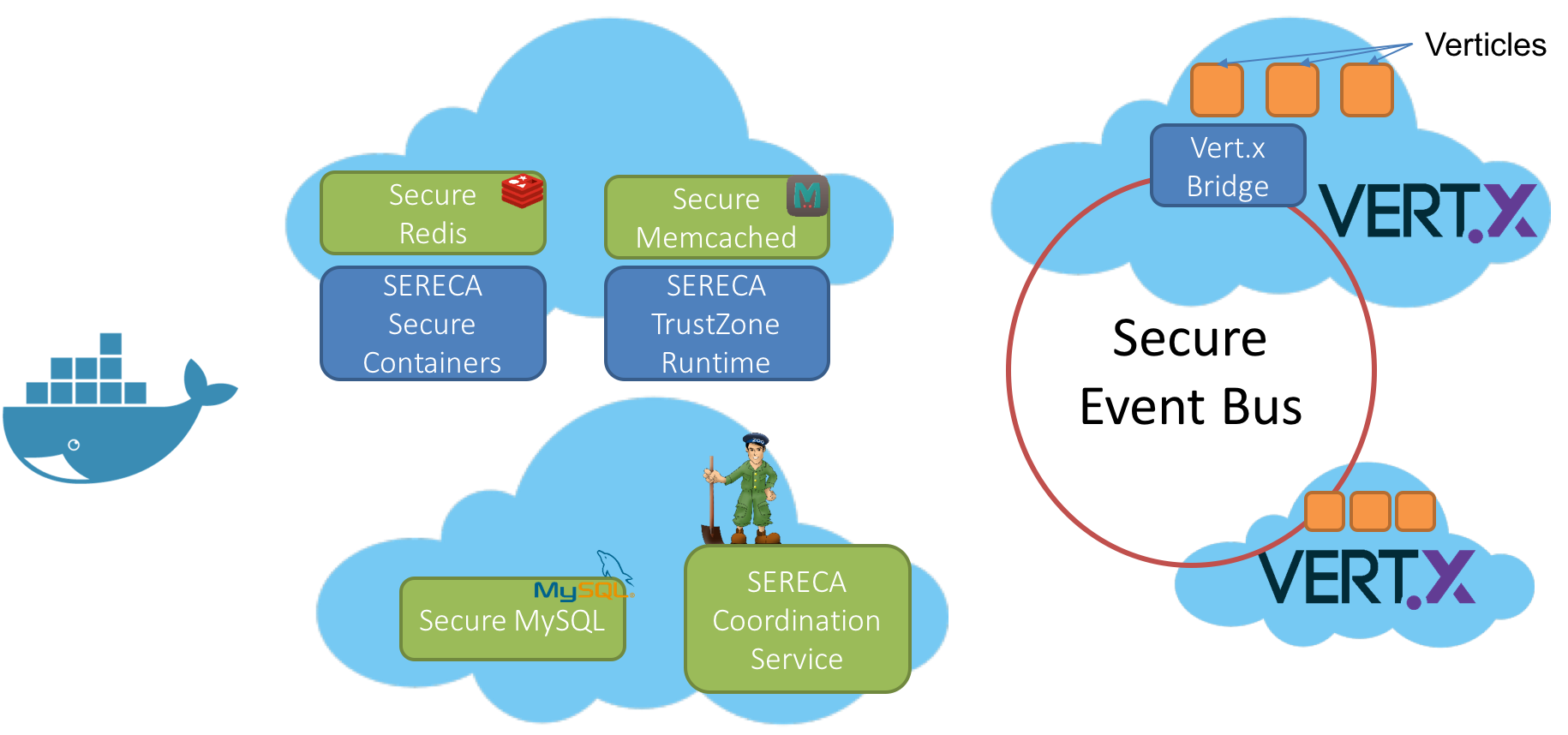
| Sichere Ausführung von Vert.X Mikro-Services | Bachelorarbeit | Dr. Stefan Brenner | abgeschlossen |
If you are interested in writing a thesis regarding this project, please feel free to contact us.